Growth is usually treated as a sign that an MSP is doing something right. More clients, broader service offerings, and larger contracts tend to be celebrated as proof that the business has momentum and relevance.
What gets much less attention is how quickly that growth
changes an MSP’s risk profile. Controls that were perfectly adequate when the team was small can start to strain without anyone noticing. Compliance expectations expand too, often indirectly, as new clients bring their own regulatory pressures into the mix.

This is not usually the result of carelessness or bad intent. It happens because growth changes the environment faster than governance, documentation, and oversight can adapt.
In this ZandaX article, we show how understanding that dynamic is the first step toward managing it properly.
Understanding the Risk Profile for MSPs
Managed service providers occupy a particularly exposed position in the technology ecosystem. They aren’t just responsible for their own internal security practices, but also play a central role in how well their clients manage risk.
As an MSP grows, that exposure widens in several directions at once. There are more systems to monitor, more users to support, and more environments that behave differently. And of course, each additional client introduces variation, and variation is where hidden risk tends to live.
At the same time, client profiles often change. For example, an MSP that began by supporting small local businesses may, over time, take on clients operating in regulated sectors without consciously “pivoting” into compliance-heavy work. These obligations arrive quietly, buried in contracts and expectations rather than formal certifications.
There is, of course, a solution! For instance, businesses in the Midwest turn to specialized MSPs
consult Midwest for IT needs to ensure their IT environments keep up with evolving regulations and best practices. Wherever you are, you should be able to find specialists in your area.
In practical terms, risk builds through inconsistency. That’s because different engineers make reasonable (but slightly different) decisions. Processes drift as teams scale. And documentation maybe doesn’t keep up with reality. On a day to day basis, none of this looks dangerous, but it creates gaps that only become visible when something goes wrong.
Strategic IT Compliance as a Growth Enabler
Compliance is often framed as something that slows organisations down. But for fast-growing MSPs, the opposite is usually true. That’s because when looked at strategically, compliance provides structure to growth rather than resistance to it. It defines what “good enough” looks like before the organisation becomes too complex to correct easily.
This means treating compliance as part of service design, not as an after-the-fact requirement. Processes are created with auditability, repeatability, and accountability in mind from the outset. And as a result, scaling those processes becomes much less painful.

If you'd like to learn more about what we provide, why not take a look at how we can help?
Boost your skills with our market-leading online courses at super-low prices.
Imagine an MSP expanding its managed security offering. dueithout a compliance, the focus is likely to stay on tooling, alerts, and response speed. Immediate, in-your-face, day-to-day stuff. But with compliance in mind, the same service is designed around evidence collection, clear escalation paths, and reporting that stands up to scrutiny.
That difference shows up quickly when clients begin asking tougher questions. And instead of scrambling to justify how things work, the MSP can explain its approach with confidence. As a result, growth becomes easier because trust is easier to establish.
The Role of Technology and Process Integration
One of the most common mistakes that growing MSPs make is assuming that more tools automatically lead to better compliance. But in reality, tools only help when they are tightly integrated with defined processes.
As headcount and client numbers rise, informal ways of working
start to break down. Risk metrics end up scattered across spreadsheets. Access reviews depend on individual diligence, and compliance evidence is rebuilt under pressure rather than captured as part of normal operations.
Integration changes that dynamic by making compliance a by-product of day-to-day work. Monitoring systems feed reporting automatically, and ticketing systems reflect ownership. As you can imagine, automation enforces consistency without relying on memory … or goodwill.
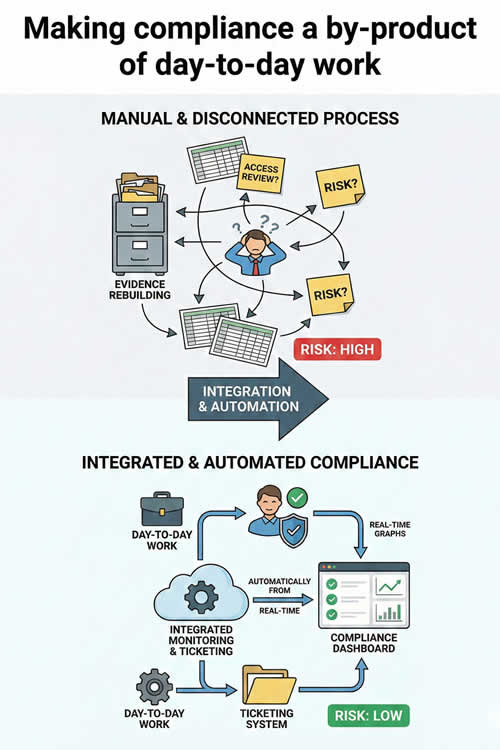
A useful way to test this is to imagine a key engineer leaving unexpectedly. If understanding how risk is managed depends on asking that person questions, the organisation is already carrying more exposure than it realises. A much smarter approach is to use integrated technology and process, which will reduce that dependency, and which becomes increasingly important as teams grow.
And it’s important to choose trusted partners. Organizations looking for managed IT services are best advised to use providers with proven track records in compliance. Specialists like
NCC Data, Plano's top MSP, personify this commitment, balancing service excellence with rigorous adherence to regulatory requirements. Working with experts like this strengthens an MSP’s overall compliance position, which of course enhances its credibility in the market.
Quantifying Risk and Compliance Impact
Risk often feels abstract because it is described in technical terms that do not connect clearly to business outcomes. This makes prioritisation difficult, particularly when management is balancing the pressures of growth against investment decisions.
Quantifying risk doesn’t require complex models or specialist jargon: it simply requires translating
technical gaps into meaningful action.
For example, a missed access review can be seen not as a procedural failure, but as an increased likelihood of unauthorised access to client systems. This would have potential consequences ranging from service disruption to breach reporting and contractual penalties. In this way, the issue becomes easier to assess and easier to prioritise.
The same applies to compliance controls. Not all requirements carry equal weight, and not all failures create the same level of exposure. By linking controls to outcomes, MSPs can focus their effort where it matters most, rather than spreading resources thinly across less important tasks.
Best Practices for MSPs Managing Rapid Growth
Here’s a quick checklist that we’ve put together at ZandaX so you can see, at a glance, the sort of things you should be doing:
- Proactive risk assessment helps identify emerging gaps as services, tooling, and client types expand.
- Client education and communication aligns expectations early and reduces friction when controls are developed.
- Continuous training ensures secure practices scale with the team, rather than relying on informal knowledge transfer.
- Leveraging automation removes inconsistency from routine compliance activities.
- Strategic partnerships provide specialist depth while internal capability is still developing.
- Comprehensive documentation turns individual knowledge into organisational resilience.
- Risk-based prioritisation ensures effort is focused on controls with the greatest potential impact.
Individually, these practices help. Together, they create a system that scales more predictably under pressure.

Expanding Compliance Frameworks for Future Challenges
Many MSPs adopt formal compliance frameworks only when they are forced to do so by a client requirement. This may be understandable, but it’s a reactive approach that often leads to rushed implementations and unnecessary rework.
A more sustainable strategy is to treat frameworks as “scaffolding” rather than constraints. Early controls and documentation can be designed in a way that supports future expansion without locking the business into heavy processes too soon. As the MSP grows, additional layers can be added deliberately. This avoids the cycle of repeatedly tearing down and rebuilding compliance structures as expectations increase.
Future challenges are unlikely to come from a single regulation. They are more often driven by overlapping client demands, evolving threat landscapes, and greater scrutiny of third-party risk. MSPs that plan for this complexity early find it much easier to adapt without disruption.
Conclusion
Rapid growth doesn’t create risk by itself, but
unstructured growth definitely does!
For MSPs, risk exposure increases whether it’s acknowledged or not. So the real choice lies in whether compliance evolves alongside the business or is left behind. Strategic IT compliance provides a framework that allows growth to remain controlled and credible. And it turns risk management into an enabler rather than a drag on momentum.
MSPs that invest early in structure, integration, and clarity tend to scale with greater confidence. That’s not because risk disappears, but because it is understood, measured, and managed deliberately.
That confidence is often what clients notice first — and what keeps growth sustainable in the long run.




























